Why You Have Open A Ticket
Google discloses salesforce instance breach due to tech support vishing campaign
Opening a ticket to get help from IT can feel like the most annoying part of your day. You just want someone to pick up the phone, fix the problem, and let you get back to work. Instead, you are forced to fill out forms, describe the issue in detail, and wait for a reply. It can feel slow, bureaucratic, and completely unnecessary, until you understand the real reason behind it. More on that later.
The Incident
A recent disclosure by Google revealed that attackers successfully infiltrated a Google Salesforce environment, one user at a time.
Credit where it’s due: Google’s disclosure was clear, detailed, and left little unanswered. The methods and motives of the attackers were well documented. This is how you disclose a breach in a thorough, airtight way, allowing your organization to move on.
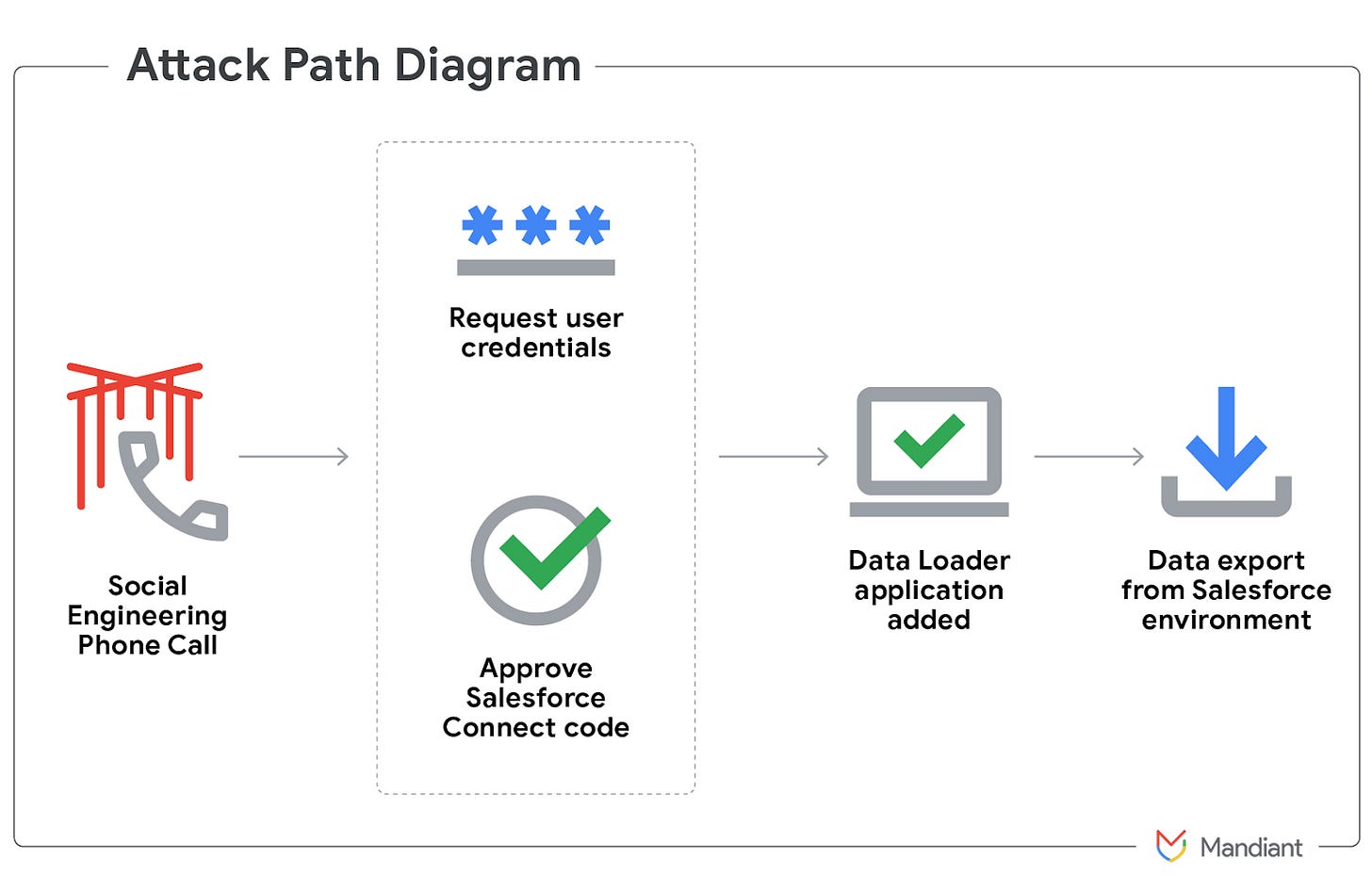
The attack vector was not the most efficient, but it was effective. The threat actors used social engineering vishing calls, impersonating tech support. Once on the line, they convinced victims to launch a Salesforce data extractor, which enabled the download of a large portion of the environment, as outlined in the report.
Leaking Salesforce data is not inherently disruptive to business operations, and scraping it one victim at a time is tedious. So why bother?
Extortion. Salesforce data can include client lists, pipeline details, financial information, and more. The attackers were likely betting that some companies would pay a ransom to prevent public release or to have the stolen data deleted. While the ransom success rate may be low, the payouts from a single lucrative target can be significant if the stolen information is sensitive enough.
Google also noted that exfiltration attempts continued for months after the initial incidents. This suggests the attackers collect data from many organizations during a campaign, then sift through it later for the most valuable details.
How can you prevent this kind of breach?
Every breach is preventable with the right awareness and processes. Training users to recognize and resist fake tech support calls is critical. This is the reason IT insists on strict ticketing procedures. “We will not call you unless you open a ticket” is not just us being annoying; it is a safeguard for your company data. It is the last line of defense against an increasingly sophisticated AI powered vishing campaigns.